The CISA Zero Trust Maturity Model is looming large on the horizon for federal agencies and contractors.
If you’re concerned about the CISA Zero Trust Maturity Model, you’re not alone. Maturity models can get confusing, especially for federal contractors and subcontractors trying to run a business and stay compliant with the evolving regulatory environment.
The good news is you’re in the right place if you’re looking for assistance with CISA’s ZTMM. As a cybersecurity solutions provider in the federal contracting space, we’re here to help you as a trusted advisor with industry-tested, cost-effective solutions.
This post is part four of a six-part series on the five pillars of the CISA ZTMM. The first article was an introduction. Since then, we’ve covered Pillar 3, Networking, and Pillar 1, Identity, in previous posts.
In this post, we’ll cover Pillar 2, the device pillar.
Here’s what you’ll learn:
- An Understanding of CISA ZTMM Pillar #2—Devices
- The Role of the Cloud in a Compliant CISA Zero Trust Architecture
- Leveraging the Cloud in a CISA Zero Trust Maturity Model
- What You Should Do Next To Protect Your Federal Contracts
Before we dive into the ZTMM Pillar 2, let’s do a quick review of zero trust architectures from the original memo from the Executive Office Of The President, Office Of Management And Budget:
The foundational tenet of the Zero Trust Model is that no actor, system, network, or service operating outside or within the security perimeter is trusted. Instead, we must verify anything and everything attempting to establish access. It is a dramatic paradigm shift in the philosophy of how we secure our infrastructure, networks, and data, from verification once at the perimeter to continual verification of each user, device, application, and transaction.
That’s an excellent level-set. Now let’s drill down into the device pillar.
What is CISA Pillar #2-Devices
From the CISA Zero Trust Maturity Model:
A device refers to any asset (including its hardware, software, firmware, etc.) that can connect to a network, including servers, desktop and laptop machines, printers, mobile phones, IoT devices, networking equipment, and more.
The term “device” covers the gamut of basically any computing entity that can connect to a communications network. That includes resources like virtual machines, applications, and services, including resources in the cloud.
The following table from the current CISA ZTMM includes three (for brevity) of the seven Function categories for the Device Pillar. This table outlines the maturity levels from traditional, or legacy, to the goal of optimal.
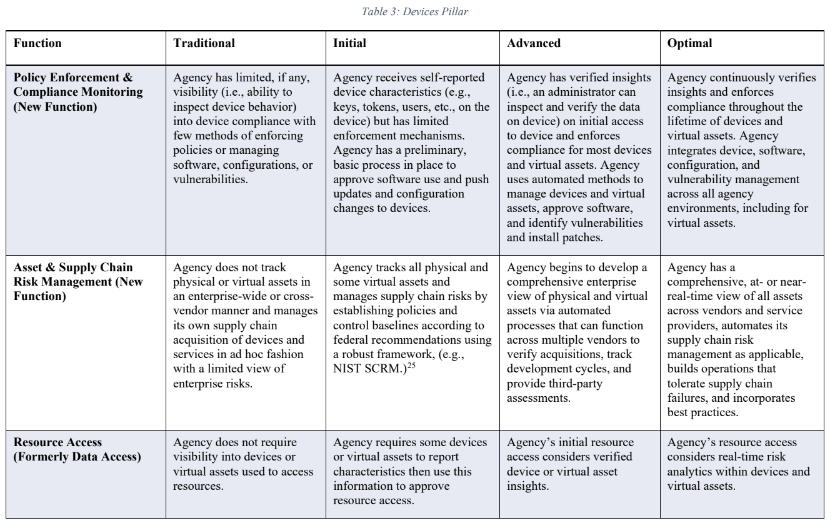
Courtesy of CISA_Zero_Trust_Maturity_Model_Version_2_508c
The migration from legacy to optimal involves several levels of continuous improvement and optimization in the areas of device monitoring, access control, and management.
What’s the takeaway? The level of constant verification, monitoring, and management of devices called for in the CISA ZTMM is a daunting task for our clients. That’s why we’re recommending they leverage infrastructure and services in the Microsoft Azure Cloud to start down the path of ZTA maturity.
Let’s talk about why.
The Role of the Azure Cloud in a CISA Zero Trust Architecture
The federal government is encouraging its agencies and customers to move to the cloud for a number of reasons. The scale and scope of the cloud’s cybersecurity infrastructure and resources dedicated to zero-trust architectures are virtually impossible to replicate with hosted or on-premise IT.
The five pillars of Identity, Device, Network, Application/Workload, and Data can’t be considered standalone entities across the continuum of ZTA maturity. This is clearly demonstrated in the Microsoft Azure Cloud resource diagram representing zero trust principles.
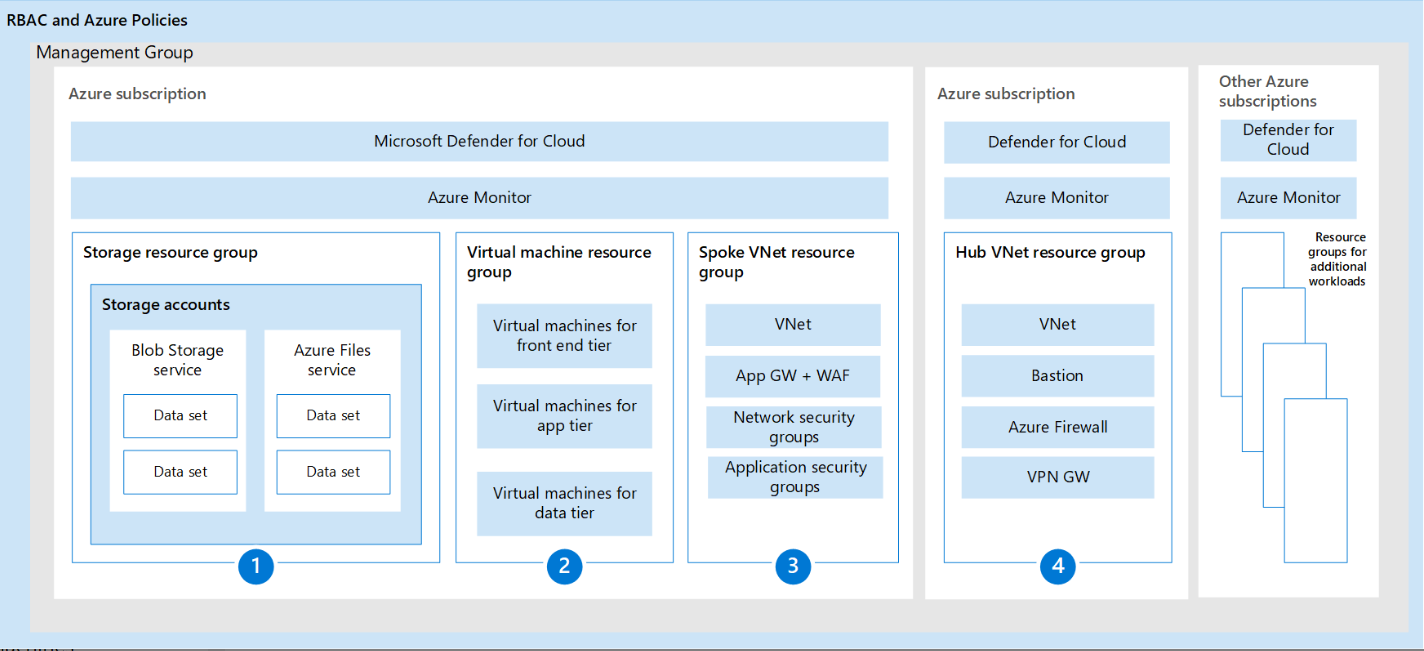
Courtesy of Microsoft – Overview – Apply Zero Trust principles to Azure IaaS
Additional data
https://learn.microsoft.com/en-us/security/zero-trust/integrate/endpoints
The role of the Microsoft Azure cloud is as shown below:
Microsoft Endpoint Manager
Microsoft Endpoint Manager, which includes Microsoft Intune and Microsoft Configuration Manager, provides protection and security for the devices that employees use and the applications that run on those devices. Endpoint Manager includes device compliance policies that ensure employees are accessing applications and data from devices that meet company security policies. It also includes application protection policies which provide application-based security controls for both fully managed and employee-owned devices.
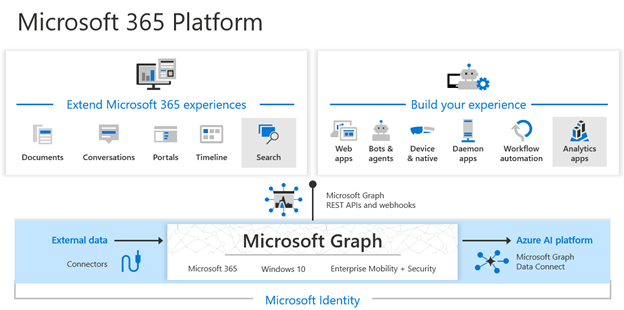
Verify devices follow security and compliance standards
ISV solutions can leverage Endpoint Manager’s device compliance and policy information to support the Zero Trust principle of Verify Explicitly. The compliance data about users and devices from Endpoint Manager allows the ISV’s application to determine a device’s risk posture as it relates to use of the application. By doing these verifications, the ISV ensures that devices using the service are compliant with the customers’ security and compliance standards and policies.
Getting Device compliance state
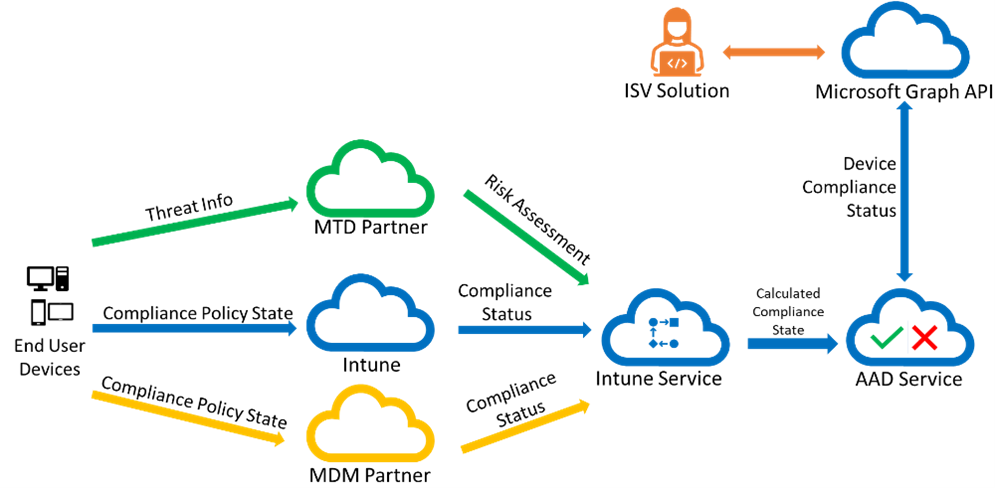
This diagram shows how device compliance information flows from the device to your ISV solution. End user devices receive policies from Intune, a mobile threat defense (MTD) partner, or a mobile device management (MDM) compliance partner. Once the compliance information is gathered from the devices, Intune calculates the overall compliance state of each device and stores that in Azure AD.
Leveraging the Azure Cloud in a CISA Zero Trust Maturity Model
Implementing the Device Pillar of a Zero Trust Architecture within the CISA Zero Trust Maturity Model involves a systematic approach that includes:
- Establishing strong identity and access management practices
- Implementing conditional access policies
- Deploying endpoint protection solutions
- Enforcing device authentication mechanisms
- Adopting a proactive approach to continuous device management and monitoring
These objectives are easily attained using at-scale, purpose-built infrastructure and services, like those available in the Azure Cloud.
We’re leveraging tools and services including Azure Active Directory with RBAC, Azure InTune for device management and control, and Microsoft Defender for device and app security and monitoring to meet CISA ZTMM Pillar 2 requirements.
Most importantly, though we are designing IT infrastructures and solutions for our clients that will provide an integrated environment designed to reach optimum maturity across all five pillars and cross-cutting capabilities. Those capabilities include:
- Automation and Orchestration
- Governance
- Visibility and Analytics
We’ve covered a lot of ground in this post, and if you’re feeling a bit overwhelmed, don’t be intimidated. The good news is our team is here to help.
Could you use some help and professional expertise in designing and implementing your ZTA?
Let’s Do a No Obligation Consultation to Assess Your CISA ZTMM Action Plan
CISA’s Binding Operational Directive, issued on October 3rd, 2022, requires action starting on April 3rd of this year. CISA also delivered an updated Zero Trust Maturity Model (ZTMM) draft on April 11, 2023, with additional guidance.
The CISA ZTMM also calls for agencies and customers to meet specific objectives by EOY 2024, which aligns with the Office of Management and Budget memorandum M-22-09, from January, 2022.
Building a ZTA that aligns with the CISA ZTMM is not an insignificant task. It takes focused expertise, knowledge, and a partner that’s always looking out for your best interests.
You probably have questions, and our team is here to provide you with the answers you need.
Call us anytime at 443.464.1589 or contact our team online today.
Have questions about Compliance?




