CISA Zero Trust Maturity Model—Addressing Pillar 1 In 2023

What is the CISA Zero Trust Maturity Model, Pillar 1-Identity, and what does it mean to Federal Agencies and Contractors in 2023?
That’s a great question, and we’ll provide the answers you need in this post.
This is part 3 of a six-part series discussing the CISA Zero Trust Maturity Model, with a separate post for each Zero Trust Maturity Model (ZTMM) Pillar.
This post will discuss Pillar 1 — Identity
Here’s what you’ll learn:
- What Is CISA Pillar #1-Identity?
- What Role Will the Azure Cloud Zero Trust Architecture Play?
- How Does the Azure Cloud Address the CISA Zero Trust Maturity Model?
- When Do You Need to Start Building Your ZTA, And What Immediate Actions Should You Take?
CKSS is a cybersecurity services provider specializing in information security and compliance services, the CISA ZTA Model, DFARS templates, Cloud Solutions, and Managed Services.
And we’re here to help you with cost-effective solutions designed and optimized for small and medium-sized businesses.
So before we get started, let’s do a quick review of what the CISA Zero Trust Maturity Model is all about. From our initial post in the CISA ZTA series:
Essentially, in a zero-trust security model, there is no implicit trust of any user, device, application, or network. Since this level of security already exists in the cloud, there is a significant push for cloud adoption by Federal Civilian Executive Branch (FCEB) Agencies and contractors.
It’s essential to remember this foundational summary as we progress through the CISA ZTA series of posts. The federal government recognizes the at-scale cybersecurity capabilities of the cloud, and they’re pushing contractors and agencies toward cloud infrastructures. More on that later.
Now let’s drill down into CISA ZTA Pillar 1
What is CISA Pillar #1-Identity?
In the latest release update of the Pre-decisional Draft, CISA defines an identity as follows:
An identity refers to an attribute or set of attributes that uniquely describes an agency user or entity, including non-person entities. Agencies should ensure and enforce user and entity access to the right resources at the right time for the right purpose without granting excessive access.
Microsoft Use Case For Implementation of an Identity Access Management Infrastructure
Azure Identity Access Management (IAM) is an overarching framework. It encompasses numerous services using:
- Single Sign On (SSO)
- Multifactor Authentication (MFA)
- Active Directory (AD) services
- Identity Provider (IdP) services
- Privileged Identity Management (PIM)
- Role Based Access Control (RBAC)
- Least Privilege Access (LPA)
- Just In Time Access (JIT)
- Just Enough Access (JEA)
The Impact of Azure Cloud’s Zero Trust Architecture: Explore Its Role
The Azure Cloud, along with AWS, GCP, and other CSPs, provides a secure network and infrastructure, a leading-edge ZTA strategy, and numerous additional cybersecurity services at scale.
As an example, this diagram below shows how an IAM infrastructure component, Azure Active Directory, forms the foundational integration platform for defining users and their access privileges and controls. Azure AD provides the IAM foundation for compliance with the continuance user authentication function in the CISA ZTMM Identity Pillar.
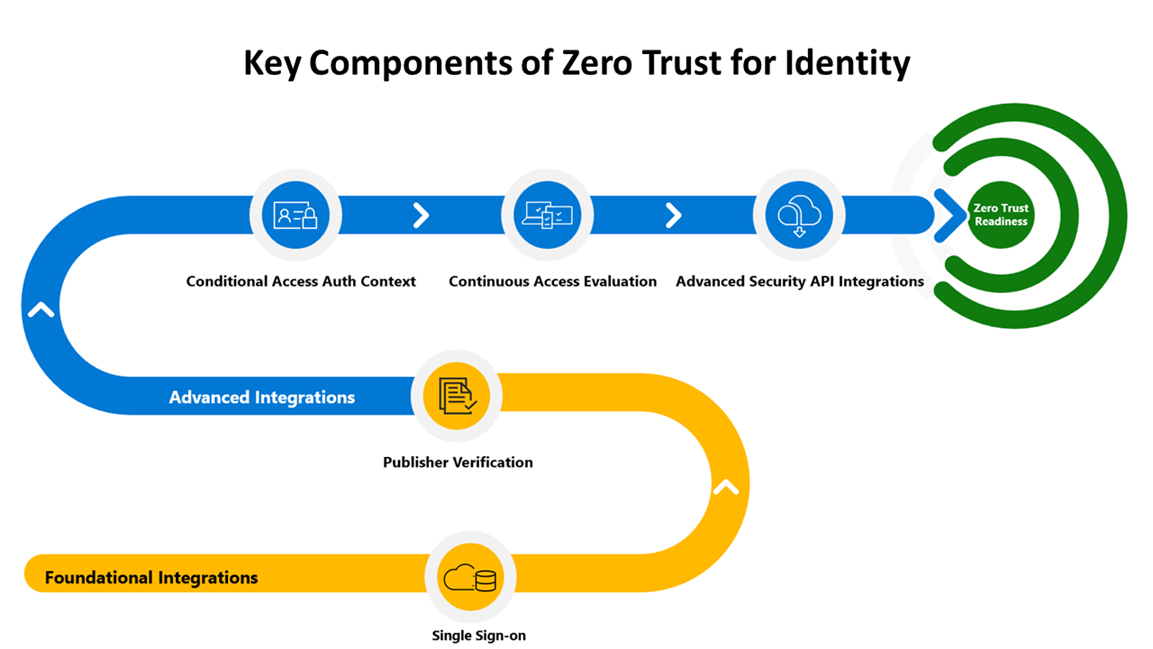
IAM Key Objectives
In the Zero Trust Model, there are three key objectives for securing your Identities and system access:
- Continuous verification and authentication of user identities and access privileges (AD, IdP, MFA)
- Continuous verification that access is compliant and typical for that identity (RBAC, LPA)
- Continuous application of least privilege access principles (PIM, JEA, JIT, etc.)
The ZTA architecture team at Microsoft Azure sums up IAM requirements perfectly:
Zero Trust is a security framework that does not rely on the implicit trust afforded to interactions behind a secure network perimeter. Instead, it uses the principles of explicit verification, least privileged access, and assuming breach to keep users and data secure while allowing for common scenarios like access to applications from outside the network perimeter.
One thing is for sure. Zero Trust is here to stay, and we don’t want any of our clients running into contracting issues due to a lack of understanding of the CISA ZTMM.
When should you start building your ZTA, and what immediate actions should you take? We’re advising our clients to perform a comprehensive end-to-end assessment of their IT infrastructure, in the context of zero trust maturity in the Azure Cloud, immediately.
CISA’s Binding Operational Directive, issued on October 3rd, 2022, requires action starting April 3rd of this year. So today is an excellent time to get started.
After you fully understand your requirements and budget, we can craft a strategy to implement a zero-trust cybersecurity architecture for CISA’s ZTMM.
It all starts with that first phone call. Our clients always tell us they feel confident and reassured after they talk with our team about compliance challenges.
You probably have questions, and we’re here to provide you with the answers you need.
Call us anytime at 443.464.1589 or contact our team online today.



