The CISA Zero Trust Maturity Model, fostered by Executive Order 14028, will have a huge impact on Federal Agencies and Contractors in 2023.
That’s a lot of acronyms and references to cross-government agencies to get your arms around!
So, if you need a refresher, we have some excellent reference material available for you. In a previous post, we discussed the genesis of the overarching zero trust maturity model from CISA, who it impacts, what the objectives are, timelines, etc.
That post discusses the intent of Executive Order (EO) 14028, the empowerment of CISA to achieve a zero trust architecture across all Federal Civilian Executive Branch Agencies by EOY 2024, and the timelines for implementation.
In this post, we’ll drill down into the “what” and the “how“ surrounding the actions that Federal Agencies and Contractors should take in 2023 to get started on the path to a ZTA.
We’re here to help you prepare to implement the five pillars described in the pre-decisional draft of CISA’s Zero Trust Maturity Model.
And we’ll start with Pillar #3-Network/Environment.
Here’s what you’ll learn in this post:
- What is Pillar #3-Networking/Environment?
- What role will the Azure Cloud play in achieving Zero Trust Architecture (ZTA) maturity?
- How does the Azure Cloud address the CISA Zero Trust Maturity Model?
- When do you need to start building your ZTA, and what actions should you take?
We’re starting with the Network/Environment pillar because your network is at the core of the five pillars designated by CISA.
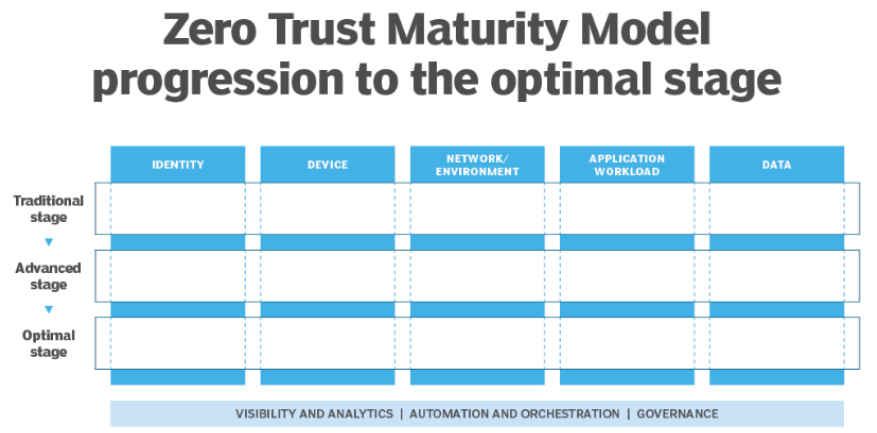
CISA Zero Trust Maturity Courtesy of TechTarget
So let’s get started with the basics.
What is Pillar #3-Networking/Environment
Here’s how CISA defines Networking in the Pre-Decisional Draft:
A network refers to an open communications medium, including agency internal networks, wireless networks, and the Internet, used to transport messages. Agencies should segment and control networks and manage internal and external data flows. Table 3 lists networks/environments functions pertaining to zero trust, as well as the considerations for Visibility and Analytics, Automation and Orchestration, and Governance within the context of networks/environments.
We’ve also included the referenced Table 3. This gives you a sense of how the three overarching guidelines of Visibility, Automation and Orchestration, and Governance intersect the Traditional, Advanced, and Optimal levels of ZTA maturity.
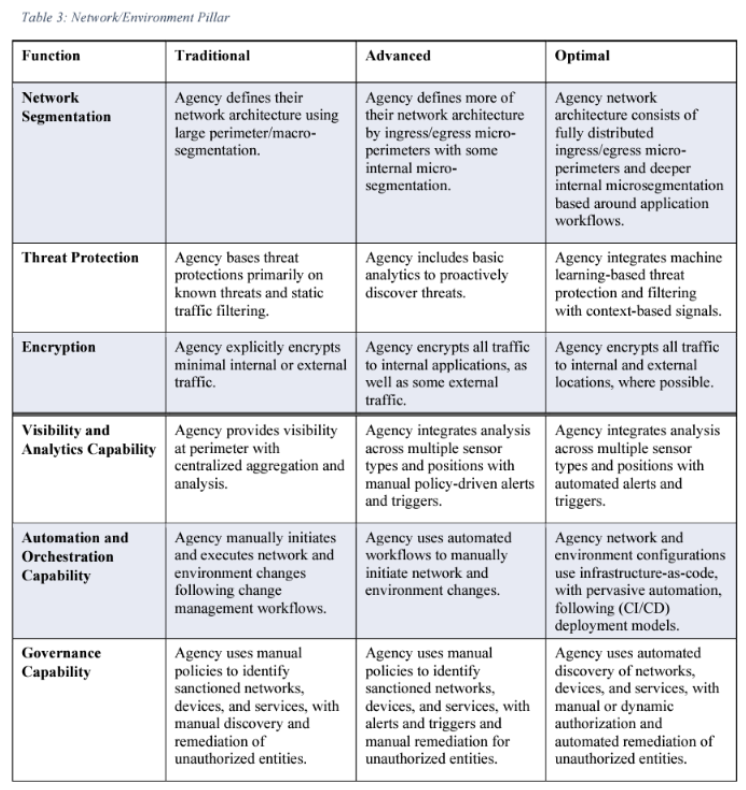
CISA Zero Trust Maturity Model-Pre-Decisional Draft
Closer examination of the table reveals how interdependent the IAM, Device, and Application pillars are, with networking at the core.
As articulated in EO 14028, it’s clear that the cloud will be an integral part of the ZTA implementation strategy achieved through the CISA maturity model.
The Use Case For The Cloud—What Role Do Azure Cloud ZTA Services Play In Achieving CISA Maturity?
The Azure Cloud, along with most of the major cloud service providers like AWS and GCP, provides essential secure network infrastructure, a leading-edge ZTA strategy, and cybersecurity services at scale. Cloud services will be essential in enabling Federal Agencies and Contractors to reach CISA zero trust maturity levels.
As the CISA zero trust maturity model rolls out, Federal Agencies and Contractors will be faced with decisions to choose various technologies, platforms, and cloud service providers to align with future ZTA maturity models and guidelines.
By virtue of hosting in the cloud, users also have the ability to leverage Azure’s at-scale infrastructure and technologies across secure virtual and geographical boundaries.
Some of the critical goals of a ZT network security strategy include—reduced threat surface areas, assertive, continuous identity and device monitoring and verification, reduced threat blast radius, prevention of lateral intruder mobility, and multiple security and identity verification endpoints.
The diagram below denotes Azure network segmentation and boundary enforcement safeguards employed to address Zero Trust networking requirements
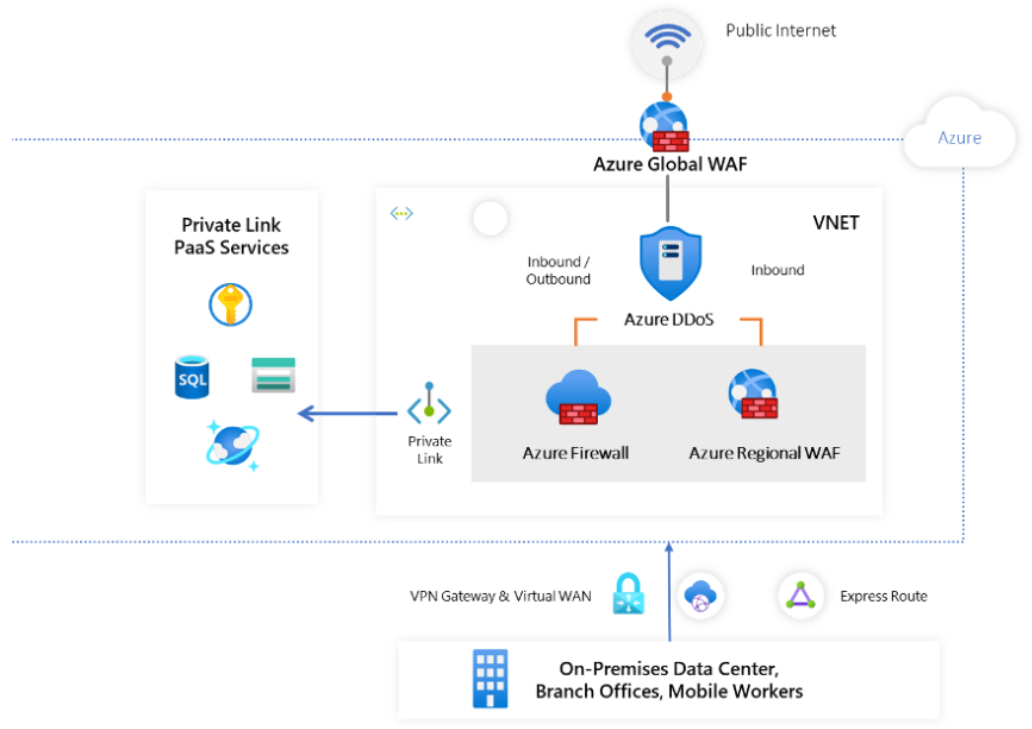
Zero trust means that you no longer assume that traffic inside the firewall is safe and trusted. In fact, a ZTA assumes that breaches are inevitable and manages network requests as if a breach has already occurred. These presumptive breaches place Identity and access management policies and practices in a critical role.
In the Zero Trust model, there are three key objectives when it comes to securing your networks:
- Be ready to handle attacks before they happen.
- Minimize the extent of the damage and how fast it spreads.
- Increase the difficulty of compromising your cloud footprint
The Azure Cloud also provides government-approved services, like the Government Community Cloud, aka GCC and GCC High, and GCC High Impact. These services allow users to use apps like MS 365 safely and securely in the government cloud.
What’s the bottom line?
The CISA maturity model is the guiding model for zero trust compliance for Federal Agencies and Contractors. And one of the shortest, most cost-effective paths to maturity and compliance is the Azure Cloud.
When do you need to start building your ZTA, and what actions should you take now?
We’re advising our clients to perform a comprehensive end-to-end assessment of their IT infrastructure in the context of zero trust maturity in the Azure Cloud.
You won’t be able to create a logical path forward until you assess your current environment in meticulous detail. This includes your applications, data, network and communications infrastructure, and devices.
CISA’s Binding Operational Directive, issued on October 3rd, 2022, requires action starting April 3rd of this year. So today is an excellent time to get started.
At CKSS, our team of regulatory compliance security specialists has extensive experience helping Federal Agencies and Commercial Clients wade through the perilous waters of federal regulations.
We’ll help you and your team implement and maintain compliant, cost-effective information security programs at all levels.
With cybersecurity, forewarned is forearmed, so get in touch with our team today.
After we fully understand your requirements and budget, we can craft a strategy to implement a zero trust cybersecurity architecture in the context of CISA’s Zero Trust Maturity Model.
We also offer strategic advisory services, security compliance templates, security, and compliance staff augmentation, and managed security and compliance services, including Chief Information Security Officer (CISO) as a Service.
You probably have questions. We’re here to provide you with the answers you’re looking for
Call us anytime at 443.464.1589 or contact our team online today.
Have questions about Compliance?




