We Empower Brilliant Minds to Achieve Great Things
CKSS and The CMMC Lifecycle
CKSS is deeply involved in every aspect of the Cybersecurity Maturity Model Certification (CMMC) Lifecycle including remediation and assessments. CKSS supports Organizations Seeking Certification (OSC) by offering consulting and audit preparation.
Our team of cybersecurity experts brings over 75 years of combined experience to enhance cybersecurity programs:
- Remediation
- Assessing
- Interpreting standards, guidelines, and best practices
This wealth of knowledge ensures that you have a skilled and versatile team supporting your CMMC journey, making CKSS the ideal choice for your CMMC Compliance needs. For more details, review our CMMC blogs to learn more about the CMMC topics.

Demystify DFARS/CMMC Regulations
We Make Cybersecurity Simpler
CKSS simplifies cybersecurity by understanding and eliminating the complexity and costs that can make it challenging. We provide the most comprehensive suite of integrated security services in the market, utilizing the best available technologies.
How CKSS Accelerates CMMC Compliance
Trusted Partner
We have demonstrated a track record of aiding our customers with common security technology solutions and frameworks: NIST SP 800-53, NIST SP 171/CMMC, HIPAA, ISO 27001, SOC2, GDPR, PCI-DSS, & HIPAA




CMMC Frequently Asked Questions
The Cybersecurity Maturity Model Certification (CMMC) is one of the most significant compliance requirements facing Department of Defense contractors today. With certification tied directly to contract eligibility, organizations handling Controlled Unclassified Information (CUI) must understand not only what CMMC requires, but how to implement it correctly, document it properly, and sustain it over time.
This FAQ page is designed to answer the most common and critical questions we hear from small and mid-sized defense contractors preparing for CMMC Level 2. From cost expectations and timelines to readiness, enclaves, assessments, and ongoing compliance responsibilities, these answers reflect real-world assessment experience, not theory.
At CKSecurity Solutions (CKSS), we focus on practical, hands-on CMMC readiness. That means helping organizations close gaps, align documentation with actual operations, define clear system boundaries, and prepare defensible evidence that stands up to third-party assessment. Whether you are just starting with a gap assessment or preparing for a C3PAO audit, these FAQs will help you make informed decisions, avoid common pitfalls, and reduce risk throughout your CMMC journey.
If you have additional questions or need support tailored to your environment, CKSS is here to help.
Level 2 (Advanced – aligned to NIST SP 800-171)
Level 2 costs are higher because it requires full implementation of controls and a third-party assessment.
Most organizations should expect total costs between $50,000 and $150,000, with higher costs applying only to large or highly complex environments.
Common cost components include:
- Gap assessment and remediation:
Typically $20,000 to $100,000, depending on how much work is needed to close gaps - Documentation (SSP and POA&M):
Often $10,000 to $50,000, based on scope and environment complexity - Third-party assessment (C3PAO):
Commonly $30,000 to $100,000, depending on system size and assessment duration
Additional ongoing costs may include annual compliance support, evidence maintenance, and required exercises.
Companies most often fail due to documentation that doesn’t match actual operations, unclear system boundaries, weak or missing evidence, access control gaps, and lack of demonstrated incident response and contingency planning. Assessments are also delayed when vendor responsibilities are unclear or staff are unprepared for interviews.
No. A gap assessment identifies missing controls. Readiness includes fixing gaps, validating controls, preparing evidence, and ensuring the organization can withstand assessor scrutiny.
No. You cannot fully inherit CMMC compliance from an MSP or External Service Provider. Even when services are outsourced, your organization remains responsible for meeting CMMC requirements. Only specific controls may be shared or inherited, and these must be clearly documented and supported with evidence during an assessment.
Yes, if the MSP understands CMMC requirements.
Timelines vary. Most organizations take 12 to 18 months, with more complex environments or cloud migrations requiring additional time. Schedules are influenced by resource availability, leadership commitment, and whether dedicated CMMC expertise is in place.
A gap assessment compares your current environment against CMMC Level 2 requirements to identify missing controls, weak implementations, and documentation gaps.
You should receive a control-by-control analysis, remediation actions, SSP observations, and a realistic roadmap with priorities.
No. CMMC requires ongoing compliance, documentation updates, and operational discipline. Continuous compliance is maintaining SSPs, POA&Ms, evidence, and controls between assessments.
Responsibility is shared between the organization, enclave provider, and any MSP or MSSP involved.
Missing evidence, misaligned SSPs, unclear boundaries, and poorly defined vendor responsibilities.
Yes. Templates can be a cost-effective starting point when writing CMMC policies.
CKSecurity Solutions (CKSS) offers cost-friendly policy and procedure templates aligned to CMMC Level 2 and NIST SP 800-171. These templates are designed for small and mid-size DoD contractors and include guidance tailoring them to your environment, helping reduce time, cost, and assessment risk.
A CMMC enclave is a segmented environment used to isolate CUI, often implemented using Cloud Resources such as Microsoft Azure or Microsoft 365 GCC High.
Common mistakes include poor boundary definition, assuming providers handle compliance, missing documentation, and unclear shared responsibilities.
CKSS focuses on hands-on readiness, remediation, and continuous compliance rather than high-level strategy alone.
CKSS partners with enclave providers while focusing on compliance, remediation, documentation, and ongoing monitoring.
Yes, advisory consultants, including RPO organizations, may support contractors during a CMMC assessment when their role is clearly defined in a shared responsibility matrix. Advisory Consultants may help clarify documentation, explain implemented controls, and support coordination activities, but they do not act as assessors, make determinations, or influence assessor judgments. Final responsibility for demonstrating compliance remains with the contractor.
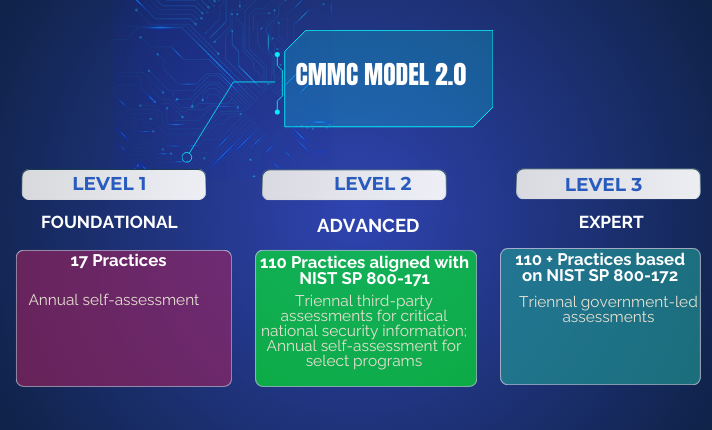
Does Your CMMC Framework Level Up?
The CMMC levels are commensurate with the type and sensitivity of information to be protected. As a result, the CMMC levels are categorized as follows:
The Evolution to CMMC 2.0
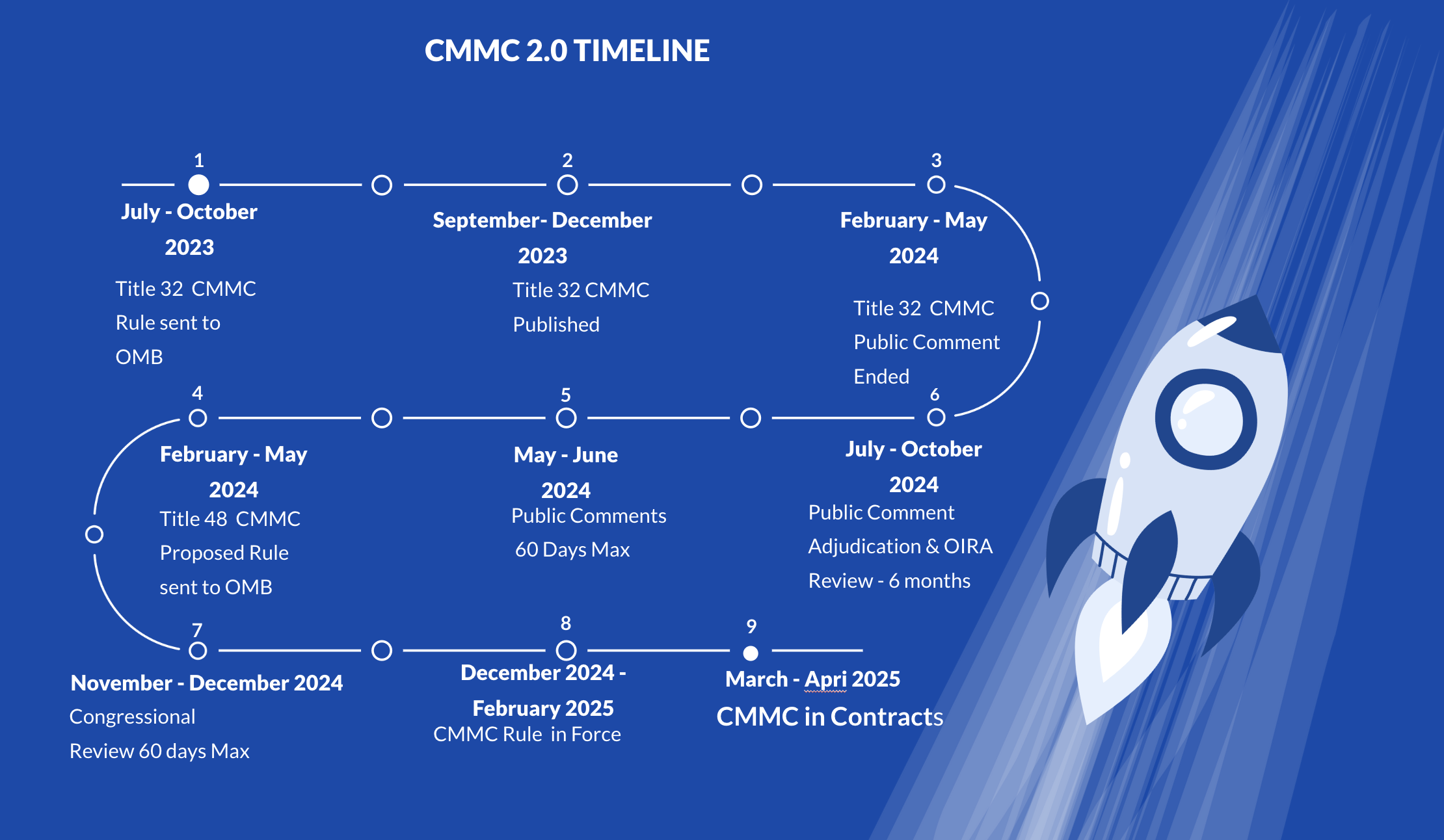
CMMC 2.0 Timeline
CMMC 2.0 is in the final phase of rulemaking and is expected to take effect by late 2024. Beginning in 2025, the DoD will gradually roll out CMMC requirements across its programs over a five-year period, eventually making CMMC compliance mandatory for all programs.
Expedite Risk Mitigation With DFARS/CMMC Compliance Templates
Combine your one-on-one consultative work with a ready to go CMMC Full Compliance Toolkit. Over 300 pages of security policies, procedures, resource plans, security plans, checklists, and bonus documents.

Cybersecurity Resources
- Whitepapers
- Articles
- Blogs
Accelerate Compliance Whitepaper
Repercussions of Biden’s Executive Order on Improving the Nation’s Cybersecurity for Federal Contractors
CMMC NIST Policy Templates: What Are The Benefits?
Trusted Memberships & Affiliations












